Overview of Scan Results
When Code Insight performs a scan of a codebase, it identifies evidence of open-source/third-party component usage, and associates that evidence with inventory items. The following diagram illustrates the relationship between codebase files, evidence, and inventory items.
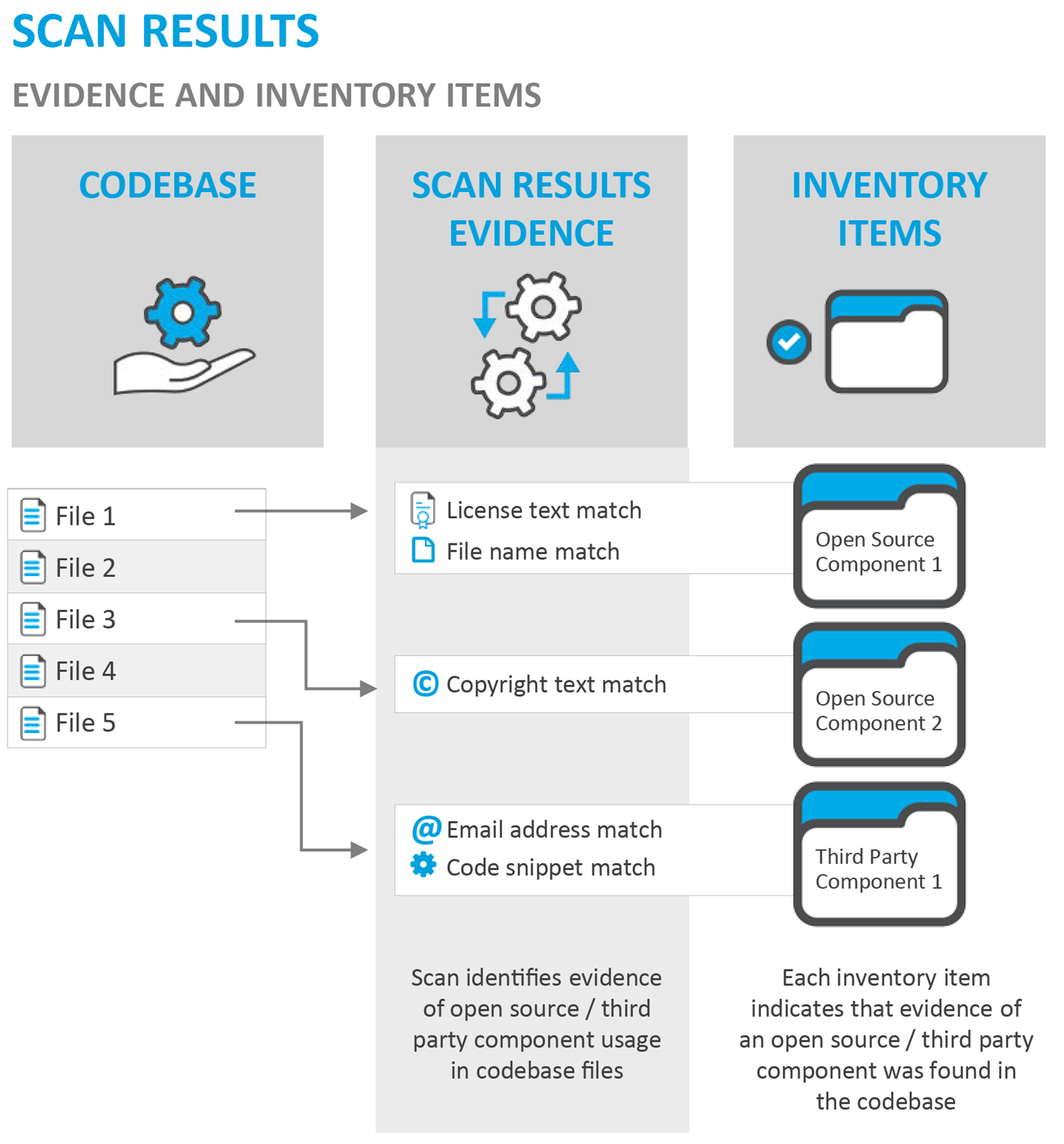
In the scan results, codebase files that contain evidence of open-source/third-party components are associated with inventory items.
Evidence
Evidence ****consists of text string matches, exact file-content matches, or code snippet matches that have been found in your codebase that identify the use of open-source/third-party components in your codebase, based upon information found in the Compliance Library (CL). The use of these components may expose your applications to compliance issues and security vulnerabilities.
Inventory Items
Inventory items associate open-source/third-party components with the files in your code base. During the scan, many inventory items are automatically created based upon defined rules, and are automatically published. Published inventory items appear in Audit Reports and are listed on the Project Inventory review page. During the audit, if the analyst finds partial matches of evidence in a file not already associated with an inventory item, the analyst can create a new inventory item to associate that evidence with an open-source/third-party component. The analyst can then manually publish the inventory item for stakeholder.
Process Flow
After the analyst performs a review of the detected evidence and inventory items, as described in Analyzing Codebase Files and Creating Inventory Items, security and legal experts in the organization need to review each published inventory item (and the discovered evidence) to approve or reject the inclusion of the associated open-source/third-party component in the software project, as described in Approving/Rejecting Inventory Items.